Untangle: WireGuard VPN
Setting Up WireGuard VPN On Mobile Devices And Desktops
https://support.untangle.com/hc/en-us/articles/360053869734-Setting-up-WireGuard-VPN-on-mobile-devices-and-desktops
Setting Up WireGuard VPN Site-to-Site Connections in NG Firewall
https://support.untangle.com/hc/en-us/articles/360055662393-Setting-Up-WireGuard-VPN-Site-to-Site-Connections-in-NG-Firewall?mobile_site=true
WireGuard VPN w/Remote Desktop
- Deploy WireGuard VPN (Roaming)
- Note assigned IP (i.e. 192.168.155.x)
- Use firewall app to restrict access to single computer
The following article from our wiki discusses the Firewall App: Untangle Wiki | Firewall
In the end, you'll probably want a rule something like this:
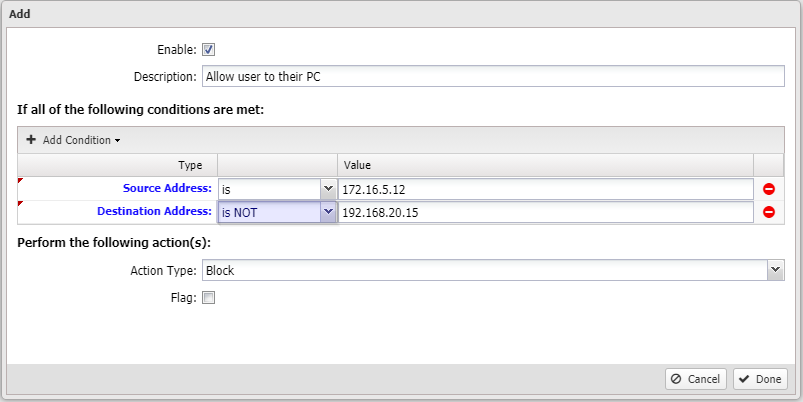
Once users connect via WireGuard, they'll be given an IP that you can use in rules as shown above.
They should be given the same IP every time they connect.
The rule above says that if traffic from that source address (the provided IP for the client that connected) is destined to anything other than the destination address specified (their PC), it should be blocked.
FAQ
Can Wireguard VPN co-exist with IPsec VPN?
Yes.
Should we bypass VPN traffic (option on IPsec)?
Yes.
In order to connect two sites (Site A to Site B) using a site-to-site VPN and assuming both sites have Untangle firewalls w/WireGuard VPN, the subnets at each site would need to be on different subnets, correct?
Correct, if they are the same the networks will conflict and break routing, so the subnet on each side of the tunnel must be different.
Is there a way to restrict roaming client VPN access to a specific computer or range of computers as opposed granting access to the entire LAN?
This can be done using Filter Rules. Each device connecting to WireGuard will get a pool IP that will not change, you can take this IP (WireGuard App > Tunnels > Remote Peer IP Address Column), then create filter rules using that as the source address and you can block/pass as you like.